Intranet Security
INTRANET SECURITY
Intranets contain sensitive, business-critical information—details about ongoing projects, personal information about employees, institutional knowledge, private conversations, and documents containing IP and other proprietary information. An intranet is exactly the type of system that requires robust security.

How intranet works
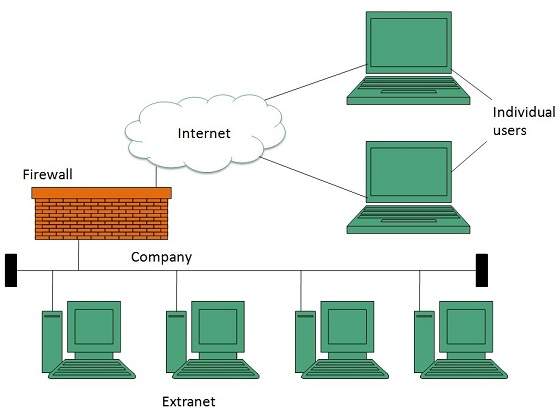
A secure and reliable intranet requires a web server that is responsible for managing all requests for files hosted on the server, finding the requested file and delivering it to the appropriate computer. A content management system (CMS) should also be set up to control the creation, publication and management of content on the intranet.An intranet may also consist of many interlinked local area networks (LANs) as well as leased lines in the wide area network (WAN). It uses TCP/IP, HTTP, and other Internet protocols (IP). Typically, an intranet includes connections through one or more gateway computers to the outside Internet.Firewall software is essential to the security of an organization’s intranet; it stands between the outside Internet and the private intranet. The firewall will monitor all incoming and outgoing data packets to confirm they do not contain unauthorized or suspicious requests, ensuring malware and other malicious attacks do not leak into the intranet.
Internal Threats
80% of hacking-related breaches are tied to weak, compromised or reused passwords.
If any user is able to view any information on the intranet, including sensitive data, it can often lead to information leaks.
While not encrypted, intranet data may be susceptible to security breaches.
Employees can enter cloud intranets remotely via their mobile devices. These devices usually don’t have reliable antiviruses or firewalls capable of protecting corporate information within public 3G, 4G or Wi-Fi networks.
External Threats
Viruses, ransomware, and spyware can attack an intranet and seriously affect its performance, for example, cause slow operating and technical errors.
Phishing attacks using tools integrated with an intranet can lure employees to disclose sensitive information like customers contacts or account numbers, which can damage the reputation of the company concerned.
These attacks are aimed at overwhelming an intranet with data requests, which makes it inoperable.
