Encryption
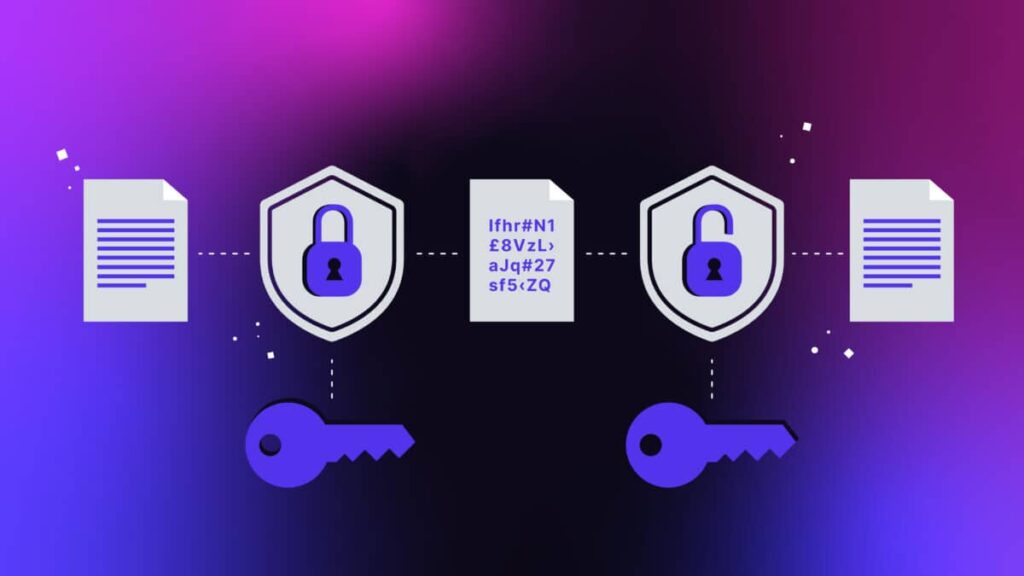
Encryption is a cybersecurity measure that protects private and personal data through the use of unique codes that scramble the data and make it impossible for intruders to read.The data encryption process is straightforward. An encryption key with a specific encryption algorithm is used to translate the plaintext data into unreadable data, also known as ciphertext. The scrambled data can only be decoded using the corresponding encryption key, so intruders will not be able to read the data when they get past the system security measures.
Why Encryption?
Attacks and security threats are the primary reason why encryption is so important in the cyber world. Many attacks are possible over an ongoing or different network whenever a connection gets established. Encryption is a way of keeping your data safe and confidential as it is sent over the internet. Whenever you send personal information across the internet, encryption stops others from seeing what you are doing.
Data is jumbled up in a manner so that when it travels through the internet it is completely unreadable, this stops hackers who may intercept the data from seeing what you’re doing.

Symmetric Vs Asymmetric Encryption
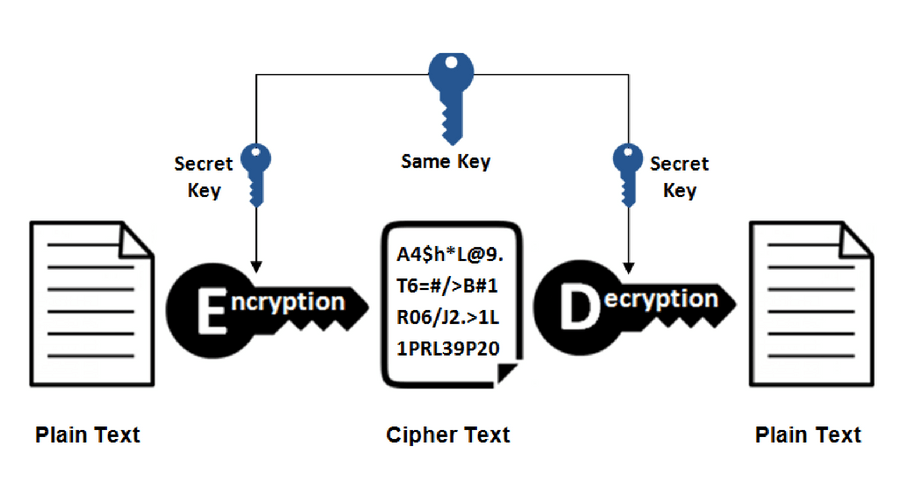
Symmetric Encryption
In symmetric algorithm, both encryption and decryption keys are the same, so the same key must be used to enable secure communication. Symmetric algorithm encryptions are commonly used for bulk data encryption and are fast and easily implemented by hardware.
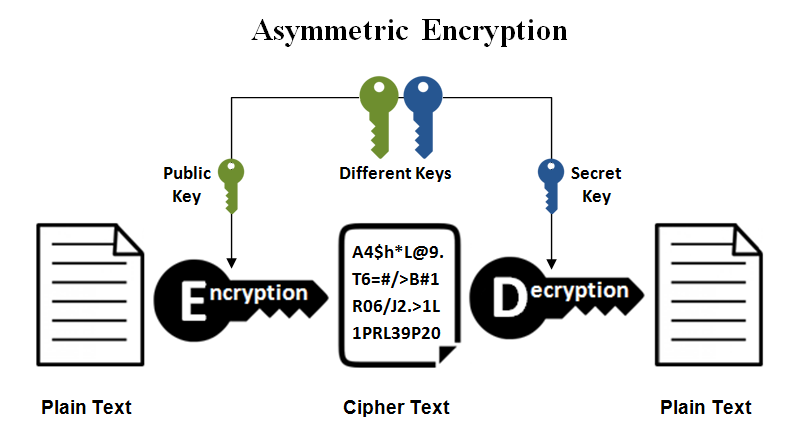
Asymmetric Encryption
Asymmetric Encryption uses a set of two keys to encode the information, a secret key, and a public key. The public key is made available to anyone who wishes to communicate with you. The secret key is kept private to the source computer/device. To decrypt any data that uses this mode of cryptography, both the keys are required, the public key and the source device’s private key.
Encryption Software Tools
One of the most popular password manager tool is Last Pass can be used for free with limited features, but will still secure your passwords and personal data. LastPass comes with an easy-to-use and intuitive interface and can simplify things for you. There are extensions available for the main web browsers, such as Mozilla Firefox and Google Chrome.This tool encourages you to set a unique and hard to break password and discourages users to reuse it.
While there are many encryption tools available you can use to encrypt your data locally, most users prefer to use Microsoft’s BitLocker software. BitLocker is a full-disk encryption tool built-in in the latest Windows operating systems (Windows 10), which uses AES (128 and 256-bit) encryption to encrypt data on the drives. The Advanced Encryption Standard has been tested and improved and is now used worldwide by the most security vendors due to its high level of security and optimization.
It is an open source program which means developers and researchers can download and use the source code.This encryption software is a great alternative to TrueCrypt tool and is constantly getting improvements and security enhancements. The new version is expected to come with lots of security and functionality improvements to better secure users’ data.
FileVault 2 is a free encryption software tool . Just like BitLocker and VeraCrypt tools, FileVault 2 (FileVault full-disk encryption) uses XTS-AES-128 encryption with a 256-bit key to help prevent unauthorized access to the information on your startup disk.
Many users are not interested in encrypting the entire hard disk, but only specific files and documents that store sensitive information. It’s a free and open source encryption software, as well as a lightweight solution known for its simplicity. This software tool is capable of extracting most archives and features strong AES-256 encryption.
CyberGhost is a popular VPN solution to ensure that your web traffic and valuable information remain encrypted. Cyberghost works with Windows, macOS, iOS, Android, Linux or routers.A VPN software program like Cyberghost can be used when trying to connect to unsafe public networks or when needed to access content whose distribution is restricted to a certain geographical area.
ExpressVPN is another VPN service you can use to encrypt your data and keep cyber criminals at bay. Similar to CyberGhost, this one uses 256-bit AES encryption technology and the set-up is simple. Compatible with multiple devices, it works on Windows, Mac, iOS, Android, or Linux .
Encryption Algorithms
Triple DES was designed to replace the original Data Encryption Standard (DES) algorithm, which hackers eventually learned to defeat with relative ease. Triple DES uses three individual keys with 56 bits each. The total key length adds up to 168 bits.
RSA is a public-key encryption algorithm and the standard for encrypting data sent over the internet. The result of RSA encryption is a huge batch of mumbo jumbo that takes attackers quite a bit of time and processing power to break.
Blowfish splits messages into blocks of 64 bits and encrypts them individually.Blowfish can be found in software categories ranging from e-commerce platforms for securing payments to password management tools, where it used to protect passwords.
In Twofish Keys used in this algorithm may be up to 256 bits in length and as a symmetric technique, only one key is needed.Twofish is regarded as one of the fastest of its kind, and ideal for use in both hardware and software environments.
AES is extremely efficient in 128-bit form, also uses keys of 192 and 256 bits for heavy duty encryption purposes.AES is largely considered impervious to all attacks, with the exception of brute force, which attempts to decipher messages using all possible combinations in the 128, 192, or 256-bit cipher.
The Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for applications, it has been highly influential in the advancement of cryptography.
